Figuring Out HTTPS MITM in India
Belonging to India, I am very used to seeing random websites being blocked. However, today was particularly scary because the MITM (Man In The Middle attack) happened over HTTPS. I visited usebottles.com over HTTPS and was served with the following page.
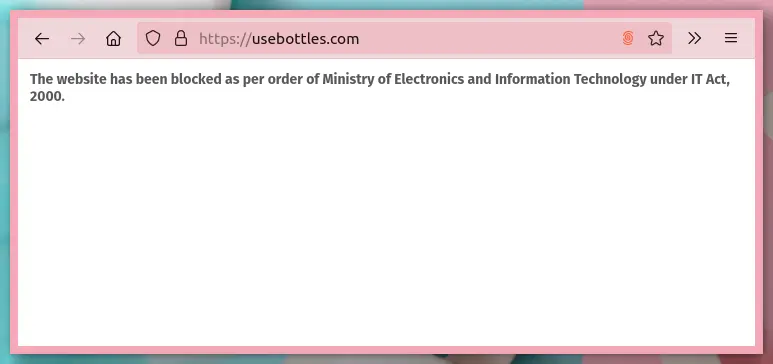
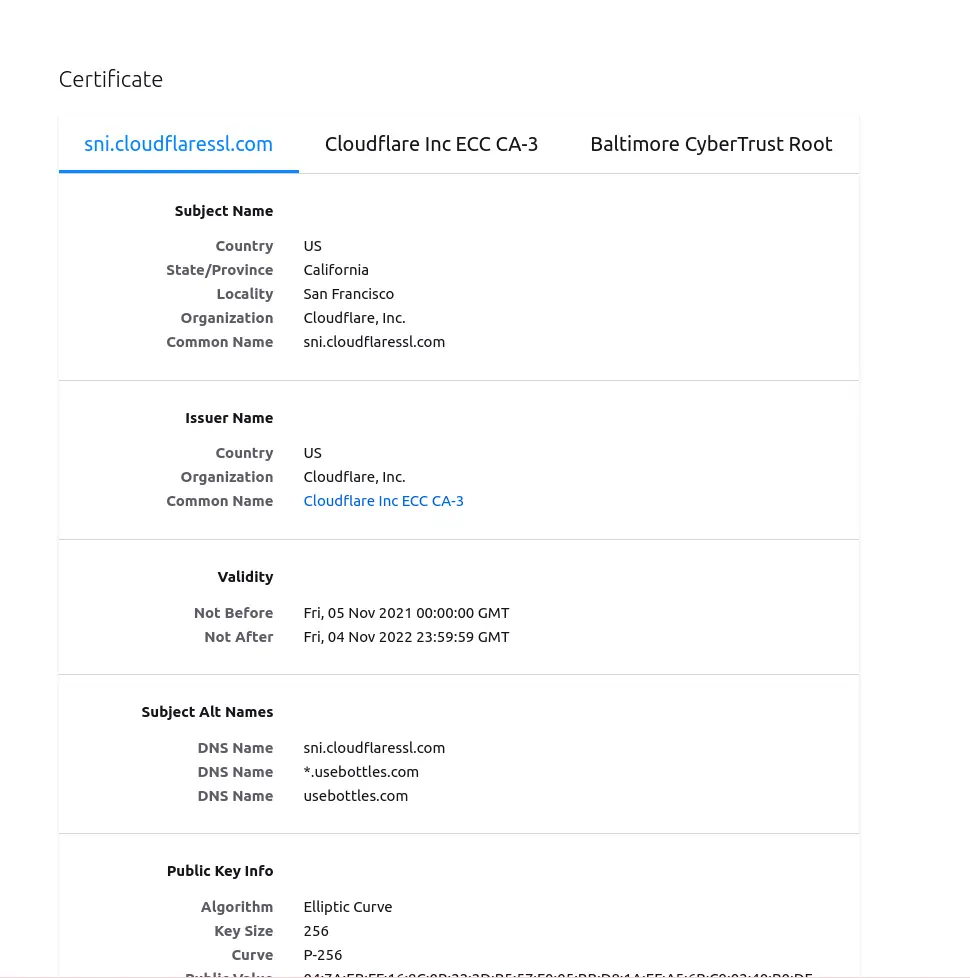
Notice the padlock in the address bar. Checking into it, the certificate is valid and signed by Cloudflare .
Further Exploration and Hypothesis#
The initial hypothesis was that the Indian Government or the ISP has Cloudflare’s signing keys and are serving the blocked page over HTTPS. This seems unlikely however and would be a very severe thing and would essentially erode all trust in HTTPS at scale as Cloudflare can sign any website’s domain which essentially means that ISPs could MITM
After a bit of exploration, the DNS entry of
usebottles.com
points to 172.67.197.25 and
104.21.92.184. I checked that both of these IPs were owned by Cloudflare. To
ensure that the DNS entries weren’t being MITM attacked either, I checked for
the same from my Hetzner Server.
The second possibility that arises from this is that Cloudflare itself was serving the blocked page. While more likely than the previous scenario, it is still unlikely generally. I looked for any notices from Cloudflare about this and could not find any.
At this point, I was mostly out of ideas. I looked into the source of the page and found something interesting. The entire page’s source was the following (invalid) HTML:
<meta name="viewport" content="width=device-width,initial-scale=1.0,maximum-scale=1.0" />
<style>
body {
margin: 0px;
padding: 0px;
}
iframe {
width: 100%;
height: 100%
}
</style>
<iframe src="https://www.airtel.in/dot/" width="100%" height="100%" frameborder=0></iframe>
The most interesting part of this was that the iframe’s URL pointed to airtel.in . Airtel is an ISP in India, however, I was not using internet services from Airtel.
My presumption is based on this.
Final Hypothesis#
This is what I presume is happening.
Me <---> Cloudflare <---> usebottles' server
1 2
So far, we have been assuming the MITM is happening at 1 i.e. between Me and
Cloudflare. However, the fact that 2 is secure isn’t guaranteed.
My best guess is that the Cloudflare server I am getting connected to happens to be using Airtel as the ISP. When Cloudflare’s server tries to connect to usebottles' server, Cloudflare gets MITM attacked by their ISP - Airtel. Likely, SSL is not enforced between Cloudflare and usebottles' server. Thus, Cloudflare connects to usebottles' server over HTTP.
Normally, a connection would happen the following way:
- I connect to https://usebottles.com/
- I get connected to Cloudflare’s server.
- Cloudflare’s server reaches out to usebottle’s server.
- usebottles' server sends a response.
- Cloudflare signs the response with the certificate.
- I get a webpage over HTTPS.
What seems to be happening is:
- I connect to https://usebottles.com/
- I get connected to Cloudflare’s server.
- Cloudflare’s server reaches out to usebottle’s server.
- Airtel intercepts the request and sends the blocking page
- Cloudflare signs the blocking page with the certificate.
- I get blocking page served over HTTPS.
I would be interested in knowing if there are any alternative explanations to this or something I have missed. You can contact me to let me know!